Comment has been collapsed.
Of course, I just wanted to quote that brilliant film :D
Comment has been collapsed.
For example, a simple search for "admin," "administrator" and "root," returned 226,631 passwords used by administrators in a few seconds.
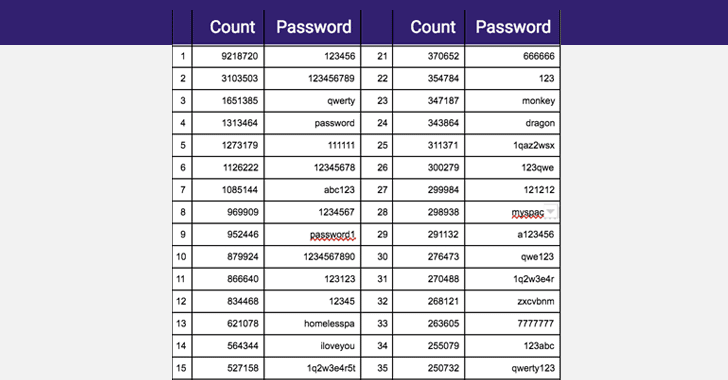
The most common yet worst passwords found in the database are "123456", "123456789", "qwerty," "password" and "111111."
Feels like you can steal half of the internet accounts without even being a hacker.
Comment has been collapsed.
Pretty much. While I was setting up networks and configuring routers for clients, you don't even wanna know what they gave me in reply when asked which password they'd like.
Comment has been collapsed.
Either that, or these 12345678 majestic combos, or simply putting down their last name as Network Name and then wanting names of their children as the pass or something of the sort which is utterly obvious and every neighbor would try first. But there were far worse combos, I just fail to remember some really good ones atm :D
Comment has been collapsed.
Intel (true key) has good password storage or kaspersky. Intel is probably more easy to use tho.
Comment has been collapsed.
Organizer? Im using one password for everything ^^
Comment has been collapsed.
I'll second LastPass. I use it all the time, I have well over 2000 randomly generated passwords saved in it. I can generate passwords in a second and when I submit a form, the password is automatically saved. Supported on most operating systems and phones.
Comment has been collapsed.
I work for a deal site where I have to check deals that users post. Part of that includes registering for websites so I have a ton of logins for various shopping sites, they add up quick. For security purposes, each site gets its own randomly generated password. That way, if that password gets leaked, it won't affect any other login I have.
Comment has been collapsed.
Damn, there we go change everything.
What will i use instead of 'password'?
Allright, from now on i will set passwords based on the numerology value of a sites name multiplied by my grandfathers name number couple with one of my cats name, one cat for each kind of site.
Comment has been collapsed.
Thats not a hard password. Add something like @§$%& or ←}► and you are save.
Comment has been collapsed.
That's actually a myth. The length is the most important element, because as long as a password can use any character, the cracker should check them. Now, for short passwords, some hackers will use dictionary attacks that run through common passwords, phrases, and words, but for anything longer than 16 characters really the length alone is a deterrent; unless you are individually targeted, the time to crack it means that whoever will just move on to the next account if necessary. Since alpha numeric is 62 possible character combinations per slot, having a 32 character password offers 2 octodecillion (US notation, and change) combinations. No contemporary machine can crack that password. That particular password is weak because it only uses elements that are guessable, but even then it is sufficiently complex that even a smart attacker (so human logic) would take hours with a good idea of how it would work.
Comment has been collapsed.
Interchanged y and z on German keyboards, time to feel safe.
Comment has been collapsed.
One can only hope that a lot of the really easy passwords are ones taken from places where people purposefully use stupid passwords... I know there are sites where I am so annoyed with them even requiring me to sign up at all that I just use something easy and stupid... But I really fear that's not the case... I know when I started needing passwords, back in the pre-internet BBS times, I felt a "safe" password was one that people would not associate with me...
Comment has been collapsed.
in all fairness, I don't think all those stupid passwords are main ones.
I've used passwords like 12345 or 'password' for throwaway accounts, or to register with websites I preferred not to register with. for stuff I actually care about, my passwords are far more complex
Comment has been collapsed.
Every day I get a authentificator message someone is trying to log in in my steam account. ^^ Without my smartphone they can go to hell.
Comment has been collapsed.
You can actually check if your accounts were compromised and if they are on their database using the following link: https://verify.4iq.com
In my case it seems like all the passwords they have for my accounts were part of a leak I've been aware for some time, and I had already changed them some time ago.
Comment has been collapsed.
Thank you. Please check the email you provided to see your results.
Your help verifying the authenticity of the data is much appreciated.
Your help verifying the authenticity of the data is much appreciated.
Your help verifying the authenticity of the data is much appreciated.
Your help verifying the authenticity of the data is much appreciated.
LOL WTF :D
Comment has been collapsed.
You can check for leaked stuff with https://haveibeenpwned.com/
Comment has been collapsed.
Where are those giveaways coming from?
17,133 Comments - Last post 54 seconds ago by Axelflox
[Intel] Free Steam/Ubisoft games (including AC ...
486 Comments - Last post 12 minutes ago by Donners
[Humble Bundle] Summer Splash Bundle🐶
15 Comments - Last post 31 minutes ago by xxxka
[Humble Bundle] July 2025 Choice (#68) 🐶
207 Comments - Last post 1 hour ago by makki
GOG | Spare codes / free games
372 Comments - Last post 3 hours ago by UltraMaster
[FREE][STEAM] 422 Soundtracks you can activate ...
201 Comments - Last post 4 hours ago by paco7533
[FREE][STEAM][ALIENWAREARENA] Ghostrunner 2 Hea...
2,955 Comments - Last post 5 hours ago by Gamy7
Happy Canada Day & 4th of July
107 Comments - Last post 1 minute ago by zolof
[OPEN] 🐒 Ace Ventura Giveaways 🐒 [140/180]
272 Comments - Last post 5 minutes ago by Ev4Gr33n
Are these overpriced games being created to far...
1,766 Comments - Last post 14 minutes ago by WaxWorm
Guess the August Humble Choice, get Clair Obscu...
85 Comments - Last post 49 minutes ago by xxxka
Guess the Game 3: Screenshot Boogaloo
17,832 Comments - Last post 1 hour ago by Riszu
Monthly PC Assistance Thread #2 July 2025
14 Comments - Last post 1 hour ago by Gusthewizard
[OPEN] Recruiting - Relaxed Giveaway Group - a ...
633 Comments - Last post 1 hour ago by CapnJ

"Hackers always first go for the weakest link to quickly gain access to your online accounts.
Online users habit of reusing the same password across multiple services gives hackers opportunity to use the credentials gathered from a data breach to break into their other online accounts.
Researchers from security firm 4iQ have now discovered a new collective database on the dark web (released on Torrent as well) that contains a whopping 1.4 billion usernames and passwords in clear text.
The aggregate database, found on 5 December in an underground community forum, has been said to be the largest ever aggregation of various leaks found in the dark web to date, 4iQ founder and chief technology officer Julio Casal noted in a blog post.
Though links to download the collection were already circulating online over dark-web sites from last few weeks, it took more exposure when someone posted it on Reddit a few days ago, from where we also downloaded a copy and can now verify its authenticity.
Researchers said the 41GB massive archive, as shown below, contains 1.4 billion usernames, email, and password combinations—properly fragmented and sorted into two and three level directories.
The archive had been last updated at the end of November and didn't come from a new breach—but from a collection of 252 previous data breaches and credential lists
The collective database contains plain text credentials leaked from Bitcoin, Pastebin, LinkedIn, MySpace, Netflix, YouPorn, Last.FM, Zoosk, Badoo, RedBox, games like Minecraft and Runescape, and credential lists like Anti Public, Exploit.in.
"None of the passwords are encrypted, and what's scary is that we've tested a subset of these passwords and most of the have been verified to be true," Casal said. "The breach is almost two times larger than the previous largest credential exposure, the Exploit.in combo list that exposed 797 million records."
"This new breach adds 385 million new credential pairs, 318 million unique users, and 147 million passwords pertaining to those previous dumps."
The database has been neatly organized and indexed alphabetically, too, so that would-be hackers with basic knowledge can quickly search for passwords.
For example, a simple search for "admin," "administrator" and "root," returned 226,631 passwords used by administrators in a few seconds.
Although some of the breach incidents are quite old with stolen credentials circulating online for some time, the success ratio is still high for criminals, due to users lousy habit of re-using their passwords across different platforms and choosing easy-to-use passwords.
The most common yet worst passwords found in the database are "123456", "123456789", "qwerty," "password" and "111111."
https://thehackernews.com/2017/12/data-breach-password-list.html
Comment has been collapsed.